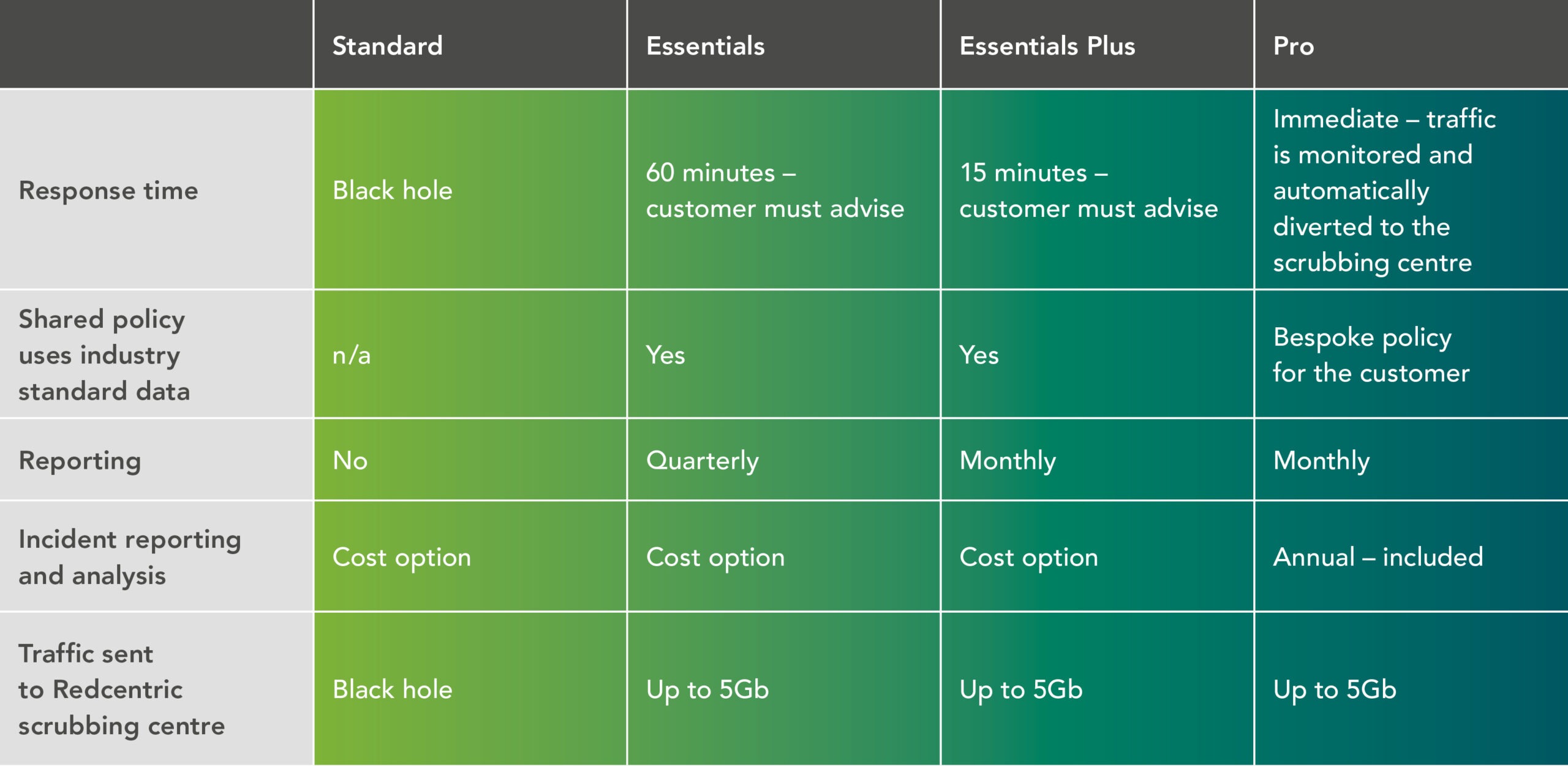
Why Redcentric for DDoS mitigation
Drawing on our profound comprehension of IT infrastructure, cloud solutions, and connectivity, we have developed a profound expertise in security as well. This unique amalgamation positions us ideally to deliver the comprehensive approach essential for assisting our clients amidst the prevailing DDoS threats.
We’ve engineered a cloud infrastructure designed to stand by you in the face of a DDoS attack, while also extending support in securing your private cloud and on-premise infrastructure. With our DDoS mitigation service, we ensure a proactive response in case of an attack, coupled with the expertise of a professional cyber team. This team aids in analysing the attack, offering guidance, and fine-tuning rules to effectively block malicious traffic in the future.